Let’s take a look at some epic social media account nightmares:
Earlier this year there was the hacking of Burger King’s twitter account that was most definitely a PR nightmare. Hackers compromised Burger King’s twitter account changing the background image to McDonald’s.
Burger King’s twitter account was only hacked for 71 minutes, but it was 71 minutes too many for the fast food giant known worldwide. During this short time period, 53 tweets were tweeted from the Burger King account resulting in 73,421 retweets. One can only imagine how many eyes read those tweets.
Burger King worked swiftly with Twitter to temporarily shut down their account and regain control of this mess; the damage had already been done—their PR disaster was making headlines around the world. However, Burger King cleverly responded when their account was back online: “Interesting day here at Burger King, but we’re back! Welcome to all our new followers. Hope you all stick around!”
Then came the hacking of the official Jeep twitter account within a day of the Burger King twitter drama. Their profile pic was changed to a Cadillac logo with the bio reading: “The official Twitter handle for Jeep – Just Empty Every Pocket, sold to Cadillac….In a hood near you!”
Several tweets were sent saying that the company had been sold to Cadillac, referencing drug use by Jeep’s CEO and employees and even racial slurs. Of course, after working with Twitter, the company eventually regained control of its account and took down the tweets and everything returned to normal.
So, these hacks were actually motivated and carried out by true hacker groups who take pride in hacking accounts like this. This raises the question of security of your company’s social media, but what if the hack isn’t by a hacker group? What if your company’s social media accounts are hacked by a disgruntled employee who actually has access to the accounts anyhow?
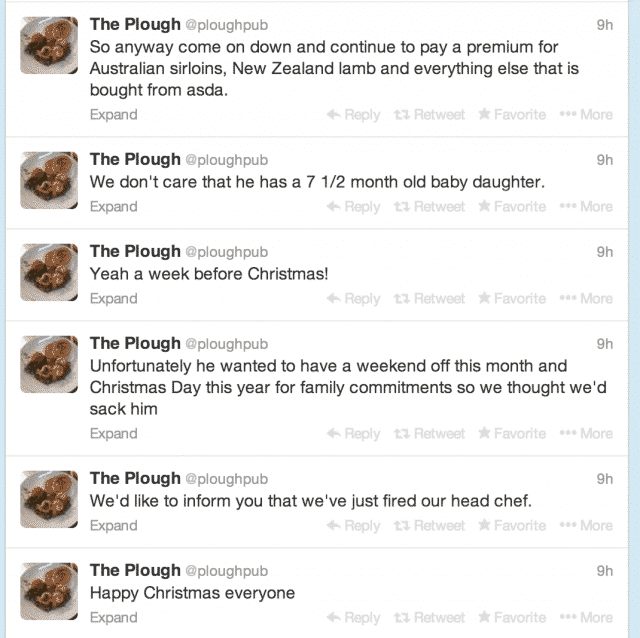
Just this month we watched Jim Knight, former head chef of The Plough, a pub in Oxfordshire, UK, get sweet revenge at his former employer at their expense via the company’s official Twitter account. This all started after Knight asked to be off on Christmas day to be with his family which eventually lead to his firing.
As you can see from the screen shot below the tweets were quite interesting:
Not only did Knight inform every one of his firing and the circumstances around it, he also outed his former employer in regarding to the quality of meat that was being sold in the pub. The situation gets even more interesting as we learn that Knight actually created with the Twitter account with permission from his former employer making Knight the actual owner of the Twitter account. This definitely puts the former employer in a tough situation. After all, the pub obviously didn’t take measures to prevent this from happening at the time of his departure. This leads to more questions about how do you secure your company’s social media to ensure situations like those described above don’t happen to your company’s social media accounts.
Here are some tips to help protect your company’s social media accounts, as well as yourself from social media disasters:
- First all don’t use easy passwords. This means making sure your passwords are ironclad. Your password should be so secure even someone who knows you extremely well would never be able to guess it. Make sure you never ever save passwords on your computer or mobile device that could be shared with others or even worse, stolen. One of the worst things you can do as well is have the passwords written down or saved on a spreadsheet–(I have seen this done before). Also, don’t use the same passwords over and over for every account. Change your passwords often as well.
- One of the best solutions for your company would be to keep all passwords hidden. There are ways that employees can be given access to social media without actually seeing the passwords. With many companies, several employees have access to post from the company’s various social media accounts on Facebook, Twitter, LinkedIn, etc. There are password management solutions like LastPass. These programs allow you to save all your passwords and distribute them to other users within your organization without the users actually seeing the actual password to the accounts. This can be very useful for multiple users.
- Be sure to know what you’re clicking on! Malicious links can also compromise your company’s social media accounts with just one click without the employee realizing they screwed up. Company’s can utilize third-party social media management platforms like HootSuite or SproutSocial to help protect against malicious links from hijacking your accounts. You can also use these to give employees access to your company’s social media accounts as well as limiting their permission levels as well.
- Another important step for security is to be sure to revoke access to the social media accounts before an employee leaves your company. This can prevent embarrassing moments like the ones discussed above.
By following the steps outlined above you can avoid a social media catastrophe that we have witnessed by so many companies. These same precautions can be used for your personal social media accounts as well. With 2013 coming to a close, what kind of social media tragedies do you think we will witness in 2014?
Image Courtesy: Social Media Keys Photo from Shutterstock, Twitter